Audit Logs - Compliance and monitoring for Fabric
Complete guide to audit logging for regulatory compliance, security monitoring, and consortium governance in enterprise blockchain networks
Enterprise Compliance Requirements
Enterprise blockchain applications must maintain comprehensive audit trails for regulatory compliance (SOX, GDPR, HIPAA), security monitoring, and consortium governance. Audit logs provide the accountability and transparency required for enterprise blockchain adoption.
Why Do Enterprise Organizations Need Comprehensive Audit Logging?
Enterprise blockchain deployments require detailed audit capabilities for:
- Regulatory Compliance: Meet SOX, GDPR, HIPAA, and industry-specific audit requirements
- Security Monitoring: Detect unauthorized access, privilege escalation, and suspicious activities
- Consortium Governance: Track multi-organization actions and maintain accountability
- Risk Management: Provide evidence for security audits and compliance assessments
- Operational Intelligence: Analyze platform usage patterns and optimize performance
Compliance Timeline
Most enterprises require 7+ years of audit log retention for regulatory compliance, with immediate access for the most recent 2 years.
How Do Audit Logs Support Enterprise Blockchain Operations?
The audit logging system maintains a comprehensive record of all platform activities, enabling enterprise organizations to monitor, track, and analyze every action performed across their blockchain infrastructure.
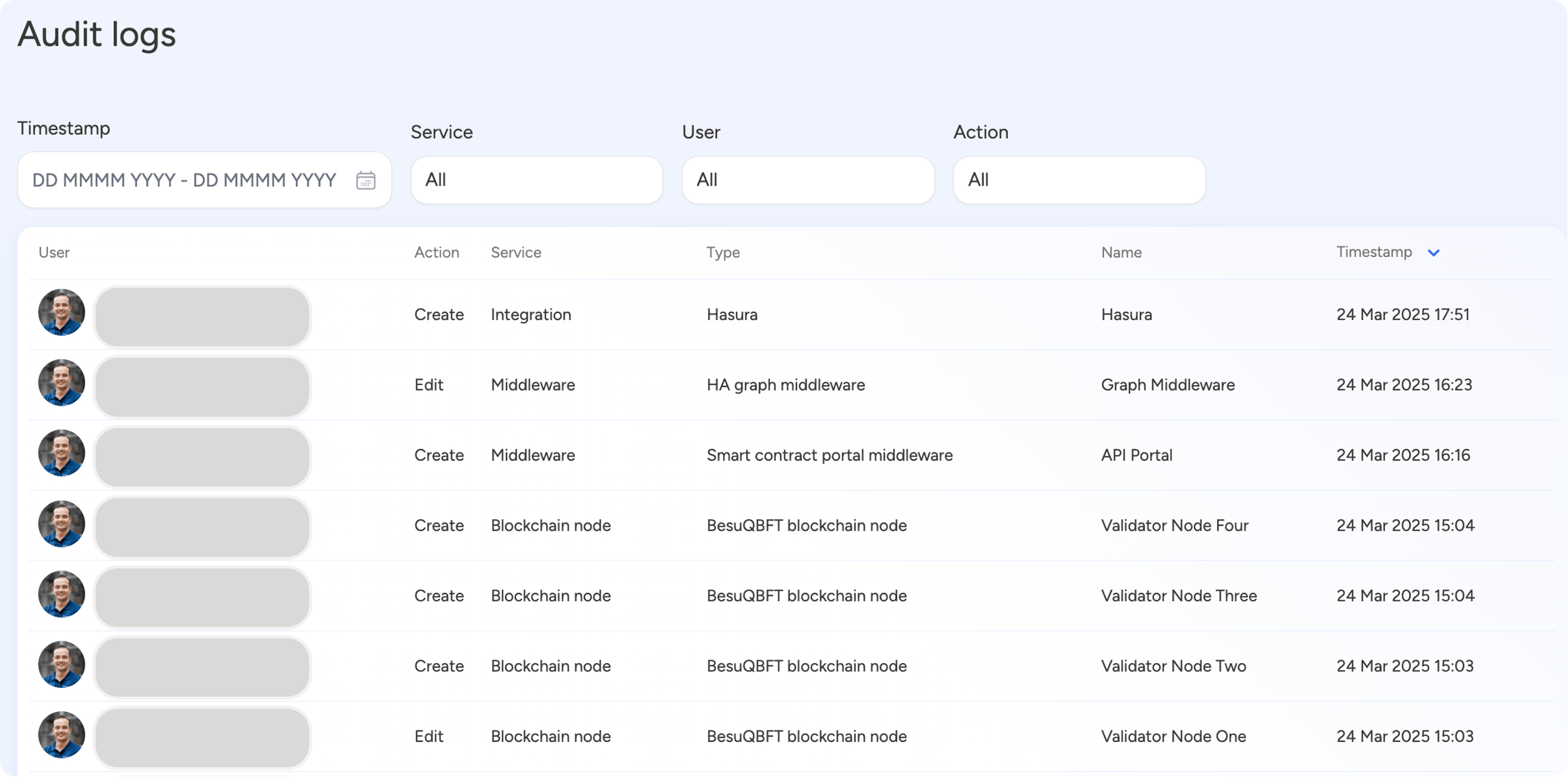
Regulatory Compliance Capabilities:
- Timestamp Precision: Microsecond-accurate timestamps for precise event ordering
- User Attribution: Complete user identity tracking with role-based context
- Action Logging: Detailed capture of all CRUD operations and system changes
- Immutable Records: Tamper-evident audit trail with cryptographic integrity
- Retention Policies: Configurable retention periods for regulatory requirements
Security and Risk Management:
- Access Monitoring: Track all platform access patterns and anomalies
- Privilege Tracking: Monitor administrative actions and permission changes
- Failed Attempts: Log unsuccessful authentication and authorization attempts
- Data Access: Record all data access patterns for privacy compliance
- Integration Security: Monitor API calls and external system interactions
Business Intelligence and Optimization:
- Usage Patterns: Analyze platform utilization and capacity planning
- Performance Metrics: Track system performance and bottleneck identification
- Service Dependencies: Monitor integration health and service interactions
- Cost Optimization: Analyze resource usage for cost management
- Capacity Planning: Predict scaling requirements based on usage trends
What Information Is Captured in Enterprise Audit Logs?
How Do I Use Audit Logs for Compliance Reporting?
Access Audit Log Dashboard
Navigate to your application's audit logging section to view comprehensive activity records across all platform components and integrations.
Filter and Search Activities
Use advanced filtering capabilities to:
- Date Range Filtering: Specify compliance reporting periods
- User-Based Queries: Track individual or role-based activities
- Service Filtering: Focus on specific platform components
- Action Type Analysis: Analyze creation, modification, or deletion patterns
Export for Compliance
Generate compliance reports with:
- CSV/JSON Exports: Structured data for regulatory submissions
- Audit Summaries: Executive reports for compliance officers
- Detailed Reports: Comprehensive logs for auditor review
- Real-time Monitoring: Set up alerts for suspicious activities
Data Retention and Privacy
Enterprise audit logs contain sensitive information that must be handled according to data protection regulations. Implement appropriate access controls, encryption, and retention policies to maintain compliance while preserving audit integrity.
Enterprise Best Practices for Audit Log Management
Compliance Checklist
Daily Review: Monitor high-privilege actions and system changes. Weekly Reports: Generate compliance summaries for stakeholders. Monthly Analysis: Perform security and operational analytics. Quarterly Audits: Comprehensive compliance and security reviews. Annual Certification: Full audit trail validation for regulators.
Integration Studio
Complete guide to using the visual workflow builder for creating enterprise APIs, business process automation, and system integrations for blockchain applications
Template Libraries
Enterprise-grade smart contract and chaincode templates that reduce development time by 80% and ensure production-ready security standards